The #1 Forensic Email Collector and Search Tool for Investigators
Aid4Mail – A fast and highly accurate email forensics tool. Superior forensic email recovery that retrieves data missed by other software.

As a forensic investigator, you face the challenge of dealing with vast amounts of email data. Traditional tools often fall short, making investigations slow and less effective. Missing crucial evidence can mean the difference between solving a case and hitting a dead end.
Imagine spending weeks on an email investigation, only to realize your software missed key evidence. Dealing with multiple email formats and service providers adds to the complexity, risking data integrity and slowing progress. The frustration can feel overwhelming, making your crucial work even more challenging.

Enter Aid4Mail, a tool specifically designed to tackle these challenges head-on. It’s fast—processing data up to 10 times quicker than its competitors. This speed transforms weeks of work into just days, without sacrificing accuracy or thoroughness.
Aid4Mail supports a wide range of email formats and services. Whether it’s PST, OST, or webmail, all are handled with ease. Aid4Mail’s versatility means you’re ready for any investigation, regardless of the data format.
Data integrity is at the heart of Aid4Mail. It preserves folder structures, attachments (including cloud attachments), and metadata exactly as they are. This ensures your evidence remains reliable and court-admissible, an essential requirement in your field.
Aid4Mail’s recovery capabilities are second to none. Retrieve deleted or corrupted emails and uncover vital evidence that other tools miss. Include cloud attachments, metadata, and deeply-nested archives. With Aid4Mail, you can delve deeper into investigations, confident that no stone is left unturned.
Use the power of AI to filter, classify, and analyze emails. Advanced filtering options, including Boolean searches, fielded operators, proximity wildcards, and more, make pinpointing specific data straightforward and efficient.
Experience Aid4Mail’s impact on investigations for yourself. The software is user-friendly and designed with simplicity in mind. Download the free trial and discover how it transforms your email forensic work. With Aid4Mail, you’re not just choosing a tool; you’re elevating your investigative capabilities to new heights.
Not convinced yet? Please read on for in-depth coverage of Aid4Mail’s many unique capabilities. It’s a long article, but you don’t have to read it all. Use the floating Table of Contents menu on the right (or below, if you’re on a phone) to jump to a section that interests you.
- A Specialized Email Forensics Tool
- A Fast Forensic Email Collector
- Superior Forensic Email Recovery
- Keyword Search and Filtering
- Accurate Email Conversion
- Ease of Use and Accessibility
- Aid4Mail vs. Other Tools
- Why choose Aid4Mail?
- Practical Applications in Forensics
- Flexible Licensing Options
- Try Aid4Mail Today
- Client Testimonials
- Glossary
Why Every Digital Investigator Needs a Specialized Email Forensics Tool
Email is still king when it comes to communication, especially in the professional world. According to Statista, around 361 billion emails will be sent daily in 2024. And those numbers keep increasing!
Why does this matter?
Email produces such vast amounts of Electronically Stored Information (ESI) that it’s usually a dominating component of eDiscovery and digital forensics investigations. Many cases have been solved by investigators finding incriminating data in email messages or their attachments. Unfortunately, suboptimal forensic acquisition tools have unnecessarily prolonged investigations and sometimes caused their failure.
Don’t make that mistake! Choosing a quality forensic email collector can make the difference between solving a crime quickly and failing to find incriminating information. This is why you should consider Aid4Mail an essential component of your digital forensics tools.
If you already use a comprehensive digital forensics tool, like Magnet Axiom, OpenText Encase, or Exterro FTK, Aid4Mail makes an excellent companion. You’ll benefit from:
- Broad Format Compatibility: Aid4Mail boasts unparalleled versatility with support for a wide range of email formats and services:
- Popular local storage solutions like PST, OST, and mbox
- Rarely supported native formats like Apple Mail and Maildir
- Cloud-based solutions like Microsoft Exchange, Gmail, and Yahoo! Mail
- Archive exports from Google Vault, Mimecast, and Proofpoint
- Blazing-Fast Processing Speed: Aid4Mail’s advanced algorithms enable you to process large volumes of local data at speeds up to 10 times faster than competing tools. With native pre-acquisition filtering and incremental processing, Aid4Mail can collect webmail up to 100 times faster than other tools. In an industry where time is of the essence, this can turn weeks of work into a matter of days.
- Unrivaled Data Integrity: In forensic investigations, maintaining the integrity of data is paramount. Aid4Mail guarantees the preservation of email metadata, message status information, and message content, ensuring that the evidence you present is always accurate and reliable.
- Powerful Recovery and Carving Capabilities: Aid4Mail excels in uncovering hidden or seemingly lost information that other products miss. Its sophisticated recovery tools can retrieve deleted or corrupted emails, and its carving feature unearths crucial evidence in disk images and extracted unallocated space.
- AI integration: Use the power of AI to filter and classify email with unparalleled accuracy, going far beyond simple keywords to understand meaning and context. AI analysis enables you to uncover critical insights through automated summarization, translation, and information extraction, freeing you from tedious manual review.
- Collect cloud attachments: Also known as modern attachments, these are files that are hyperlinked from an email but hosted by a cloud-service provider. Aid4Mail is among the very few forensic email collectors that support cloud attachments and, at the time of writing, the only one to collect from both Microsoft and Google’s platforms.
- Accurate Email Conversion: During forensic email collection, Aid4Mail accurately converts your data to formats that are easily imported into your primary investigation tool—for example, PST, MSG, mbox, EML, or CSV files.
A Comprehensive Forensic Email Collector
A professional forensic email collector must support a wide range of file formats and service providers. It should also be optimized for speed to efficiently handle large volumes of data in a reasonable time. And it must do all it can to preserve data integrity during the collection process, and report issues when they occur.
Aid4Mail is optimized for speed and stability. It can work through terabytes of data without user intervention. Aid4Mail performed 6 to 10 times faster than its competitors in tests with local files. For example, a forensic email collection taking a week to complete with a competing solution would require just one day with Aid4Mail—a considerable time-saving!
With Aid4Mail, you’re in complete control of your data, and all processing is performed on-premises. This is safer because it avoids sharing sensitive data with third-party service providers. It can also significantly reduce costs by avoiding additional fees based on the volume of data processed.
Support for Most Email Formats and Services
Local Email Storage
The following file formats are supported:
- PST, OST, and MSG files from Microsoft Outlook
- OLM files from Outlook for Mac
- Mbox files from Mozilla Thunderbird, Google Takeout, etc.
- EML files, used to store a single email message
- Maildir files in native format from an IMAP server
- Apple Mail (EMLX) in native format
Aid4Mail can process PST and MSG files with or without Outlook. It’s noticeably faster with Outlook, and you can further reduce processing time by using native filtering. We’re not aware of any other PST forensics tools offering this capability.
Aid4Mail integrates an advanced email parser that can accurately extract emails from corrupted mbox files. This is essential because of the prevalence of damage in those types of mailboxes.
Note that some competing products claim to support EMLX files from Apple Mail. Our tests found those claims to be misleading, resulting in significant data loss. We’re confident that Aid4Mail is the only forensic email collector that can accurately extract Apple Mail messages with all their contents and metadata.
Microsoft Outlook and Exchange
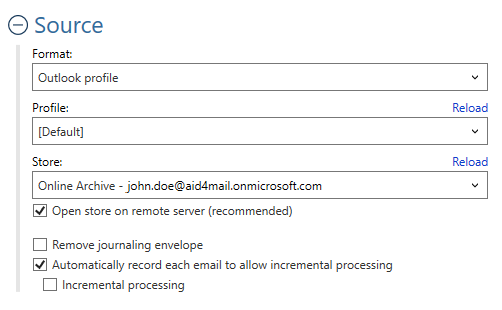
Aid4Mail provides several methods to collect emails from Microsoft Outlook and Exchange accounts. You can access the account through an Outlook profile (using MAPI), the IMAP protocol, or Microsoft’s Graph API. Each method offers native pre-acquisition filtering, which can significantly speed up forensic email collection.
Note that, to collect mail from Exchange Online Archives, and Public and Shared folders, you must use an Outlook profile.
Webmail Service Providers
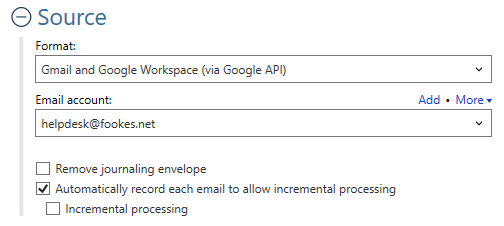
Collect emails from all webmail service providers that support the IMAP protocol. These include Microsoft 365 (formerly Outlook 365), Gmail, Yahoo! Mail, AOL, etc. Aid4Mail can also access Microsoft and Gmail accounts directly through their respective APIs. Fast native pre-acquisition filtering is available for all these accounts.
Aid4Mail supports the OAuth2 login protocol, enabling secure access to your (or your custodian’s) webmail accounts.
Remote Authentication
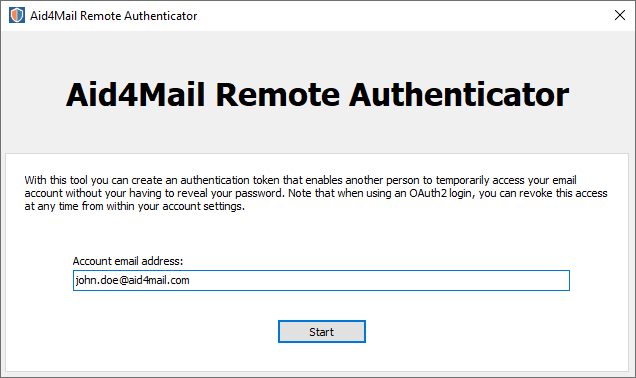
Collecting email from your custodians’ cloud-based accounts is made easier with Aid4Mail Remote Authenticator—a free stand-alone utility that they can download and run without installation. It enables the account owner to grant Aid4Mail secure, temporary access to their email service or IMAP account, without providing full login credentials or needing a copy of Aid4Mail.
Archival Formats
Aid4Mail can extract mail from the following archival formats:
- Google Takeout
- Google Vault exports (zipped MBOX files)
- Mimecast exports (zipped EML SJF or EJF files)
- Proofpoint exports (password-protected zipped EML files)
Note that you’ll need the Investigator or Enterprise edition of Aid4Mail to process Google Vault exports, and the Enterprise edition to process Mimecast and Proofpoint exports.
Unknown Formats
Aid4Mail Investigator integrates a powerful file carving tool that can extract whole or partial emails stored in MIME format, from any uncompressed file type. It can also carve emails from uncompressed disk images or forensically extracted disk space. This includes double-deleted files, slack space, and unallocated space.
Traditional and Cloud Attachments
Like many email forensics tools, Aid4Mail is able to collect files attached to an email in the traditional manner. However, it goes much further than most, into new territory—Aid4Mail enables the collection of cloud attachments (a.k.a. modern attachments) and their metadata from any of its supported formats. You can decide whether to collect multiple document revisions or only the latest version, and set a size limit for maximum efficiency.
If access to a cloud attachment requires login credentials, these can be provided to Aid4Mail for both Microsoft and Google accounts. Aid4Mail uses secure OAuth2 authentication, and also supports the remote authentication of custodian accounts.
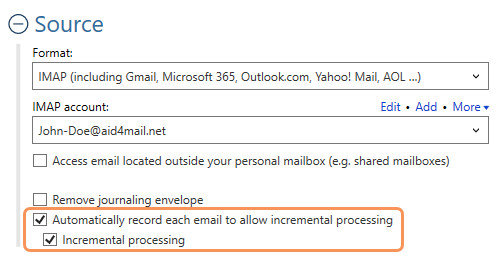
Incremental Processing (Differential Acquisition)
Processing errors typically relate to:
- Server timeouts, overloads, or bandwidth limits
- Lost internet connections
- Insufficient free disk space on the target drive, etc.
This is where incremental processing (differential acquisition) comes to the rescue. Aid4Mail identifies the emails that have been added since (or missed during) the last cycle and processes only them. In other words, it lets you pick up where you left off; no need to start all over again.
Aid4Mail offers incremental processing for all supported email formats and performs it natively, server-side, when collecting from cloud services like Microsoft 365, Gmail, and Yahoo! Mail.
This ability is usually missing in other tools. It is a significant time-saver because Aid4Mail can determine whether it has already processed an email before downloading it. As a result, resuming an aborted acquisition is very fast and reduces the risk of reaching those dreaded service bandwidth limits.
Built for Speed
Processing Local Files
Aid4Mail is highly optimized for speed without sacrificing reliability or accuracy. When processing local mailbox files, it can parse, collect, and convert emails up to 10 times faster than competing email forensics tools—a considerable time-saving!
We conducted speed tests using a standard ASUS laptop (2022 model with an AMD Ryzen 9 5900HX processor and an internal SSD drive). Our tests included converting the publicly available John Podesta email collection, a 5 GB file containing 50,887 emails.
In our first test, Aid4Mail converted the Podesta emails from mbox to Outlook PST in 2 minutes and 59 seconds. That’s a rate of 284 emails per second!
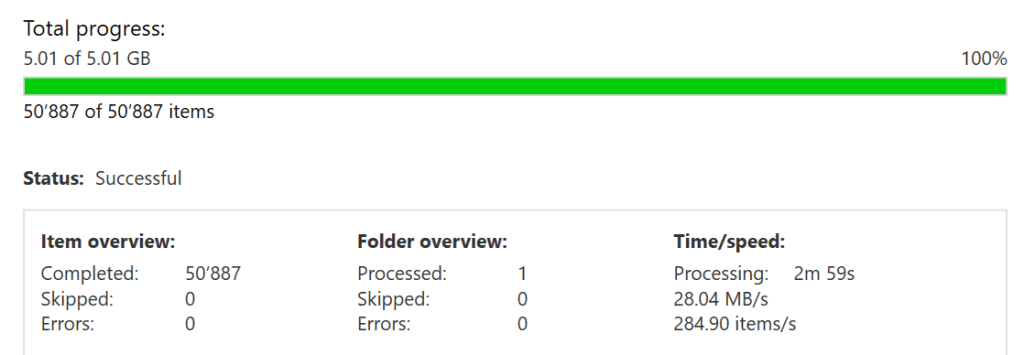
In our second test, Aid4Mail converted the same data from PST to mbox in 8 minutes and 10 seconds, a rate of 103 emails per second. The slower performance in this second test is due to additional processing to preserve metadata and improve conversion accuracy. Despite this, Aid4Mail still performed faster than competing tools. With a high-end computer, you can expect even better results.
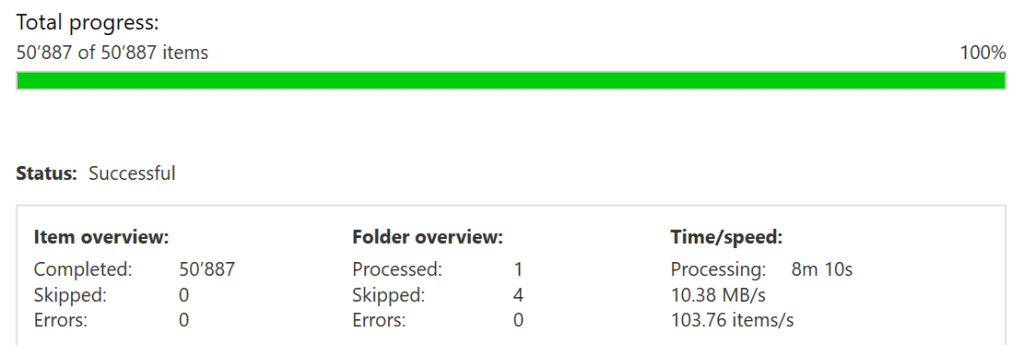
Note that you can download the Podesta mbox file from the internet for free. Use it to test your current digital forensics tool and compare its performance with Aid4Mail. We’d be happy to provide you with a download link if you can’t find it. Just contact us with your request.
Remote Accounts
Aid4Mail is optimized for cloud-based email accounts, offering two time-saving features often missing in other tools. Both involve native, server-side processing of emails and are covered in the following sections:
With these capabilities, Aid4Mail can collect emails up to 100 times faster than tools without them.
Concurrent Processing
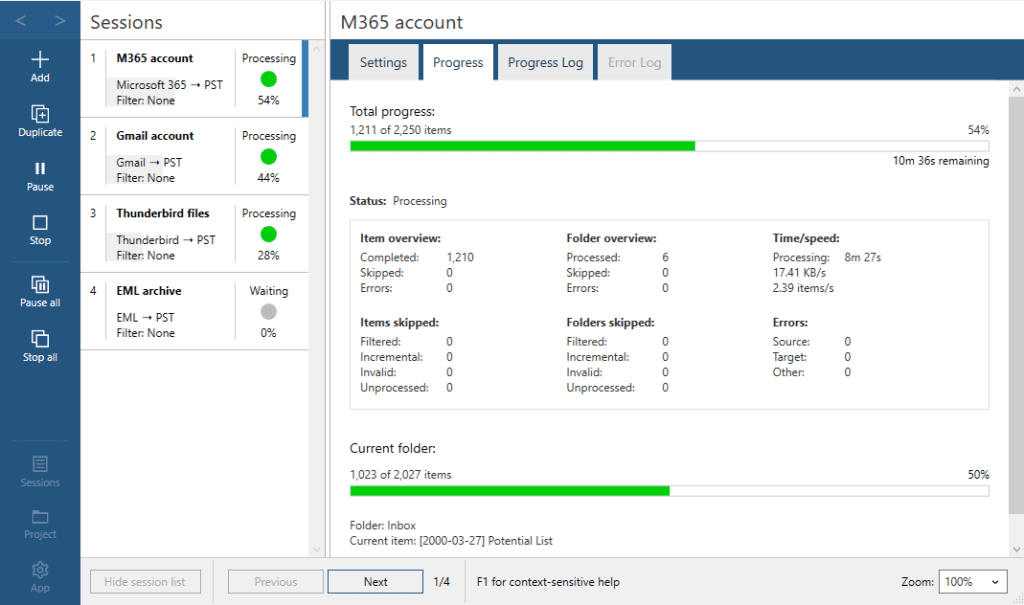
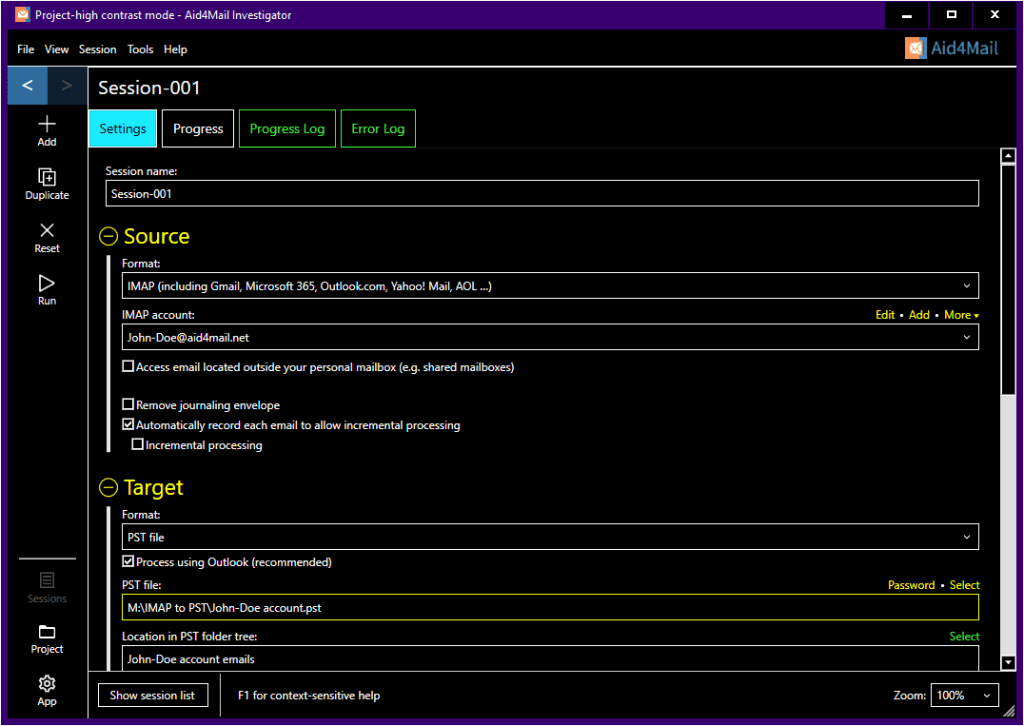
With Aid4Mail Investigator and Aid4Mail Enterprise, you can run multiple processing tasks simultaneously, taking full advantage of your computer’s hardware and saving more time. Consider a scenario where you need to collect email accounts from several employees under investigation, or one where you need to gather multiple source formats from a single custodian.
For example, you might need to collect data from a custodian’s Microsoft 365 account, Gmail account, local Thunderbird files, and archived EML files, and combine them into the same batch of target PST files. With Aid4Mail, you can set up the project in advance and let it run overnight so that no time is wasted.
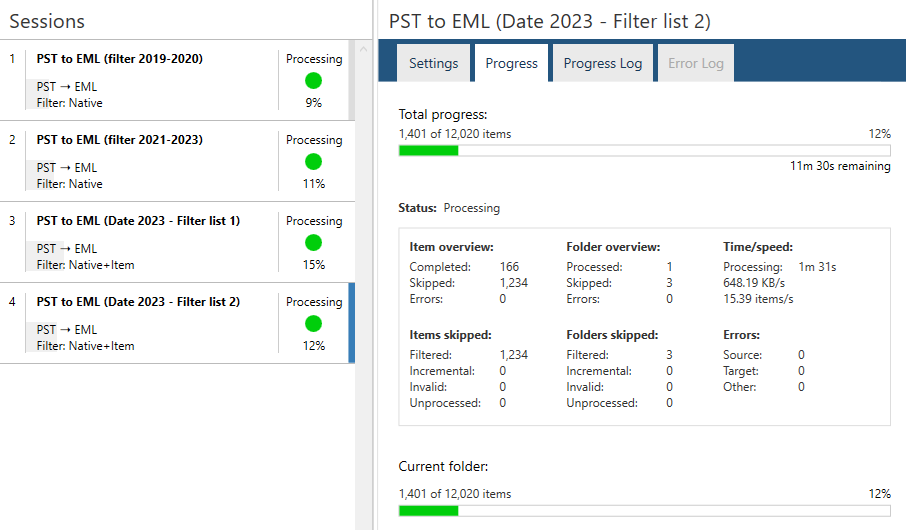
Alternatively, you may have four tasks that use the same input but require different filters, with the results output to separate folders within the same PST file. In Aid4Mail, all four tasks can be run concurrently, and unattended, while you are working on something else. You can see an example of this in the screenshot below.
Data Integrity
Data integrity and preservation are essential parts of digital forensics. Without them, you risk compromising your case due to loss of evidence. Large mbox files and Outlook PST files often contain data corruption, and some email client programs worsen the situation by deviating from format standards in undocumented ways. Even fully intact email is vulnerable to data loss during collection, format conversion, and target storage.
Aid4Mail stands out from other digital forensics tools in its ability to maintain data integrity. It is built on a foundation of 25 years of email processing, significantly longer than other email forensic tools on the market. Not only does Aid4Mail avoid data loss during processing, but it can usually repair pre-existing data corruption, and work around non-standard file format implementations.
Folder Names and Structure
Preserving folder structures and names during mail collection helps to quickly distinguish between emails like Sent, Drafts, Deleted, Spam, and Received messages. It also reveals how custodians grouped and organized their incoming mail. This makes it easier to sift through extensive email collections and find clues to the most significant messages.
Aid4Mail lets you include or exclude folders during the acquisition process. This can significantly speed up email collection, especially if you can exclude large folders with unnecessary content. However, folder filtering only works reliably when based on an accurate representation of the source account. Aid4Mail provides this.
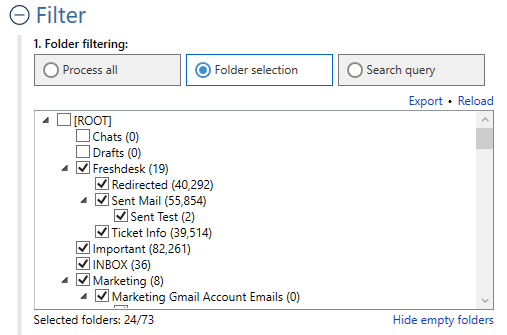
Aid4Mail excels at preserving data integrity with respect to the email folder structure. It particularly stands out among other solutions when handling Google Takeout files, Google Vault exports, Maildir stores, and local Thunderbird mailboxes. This is because Aid4Mail understands the unique implementations of these formats and is able to work with (or around) them.
Attachments and Embedded Contents
During email collection, certain storage formats have a higher risk of data loss of attachments and embedded content. This concerns formats that don’t store or deliver emails in native MIME format; for example, Apple Mail EMLX files, Thunderbird and RFC 1521 emails with detached attachments, and emails acquired through Microsoft Outlook.
Again, Aid4Mail understands the unique implementations of all these formats. Unlike many forensic acquisition tools, it handles them correctly and recovers their attachments (as long as they haven’t been moved or deleted).
Header Metadata
If processed incorrectly, specific email formats and protocols are susceptible to loss of header metadata. This occurs when collecting messages through Outlook’s MAPI protocol or accessing MSG, OST, and PST files through third-party DLLs.
We’ve seen results from forensic email collectors that lost important information including:
- Email addresses
- Sender’s time zone
- IP address
- Server relay information
- Original Message-ID
- Thread index
This level of data loss is potentially disastrous when performing email header forensics. You can easily avoid these serious issues by using Aid4Mail.
Email Status Information
Email status information tells you about the actions taken on a received message. For example, whether it was read, replied to, or forwarded. It also indicates the status of an outgoing message, whether it is still a draft, unsent, or sent. Emails can also be flagged (or starred), and marked as double-deleted. This is crucial information as it provides valuable insights into the lifecycle and interactions associated with an email.
Some forensic acquisition tools do not collect email status information at all, or only partially collect it. Aid4Mail stands out again by preserving this important data, whether the emails are obtained from cloud-based accounts or from local stores such as Google Takeout, OST, and PST files.
Format Errors
There are many different email client programs and cloud-based systems for sending messages. Unfortunately, some don’t fully respect standards, or they contain bugs that produce email format errors.
We have encountered a considerable number of these format errors during our many years of creating email solutions, even from companies like Microsoft and Google. The result of our extensive experience is that Aid4Mail can fix many of these errors, ensuring emails and their metadata render without data loss.
Progress and Error Reporting
Aid4Mail provides detailed progress information and error reporting to ensure a smooth experience. You can track the progress of your task through real-time indications of both the amount of data processed and the estimated time to completion. You have access to a detailed progress report and, when necessary, an error log. The software displays various counters indicating how many folders and emails have been collected, excluded by your filter criteria, and failed due to errors.
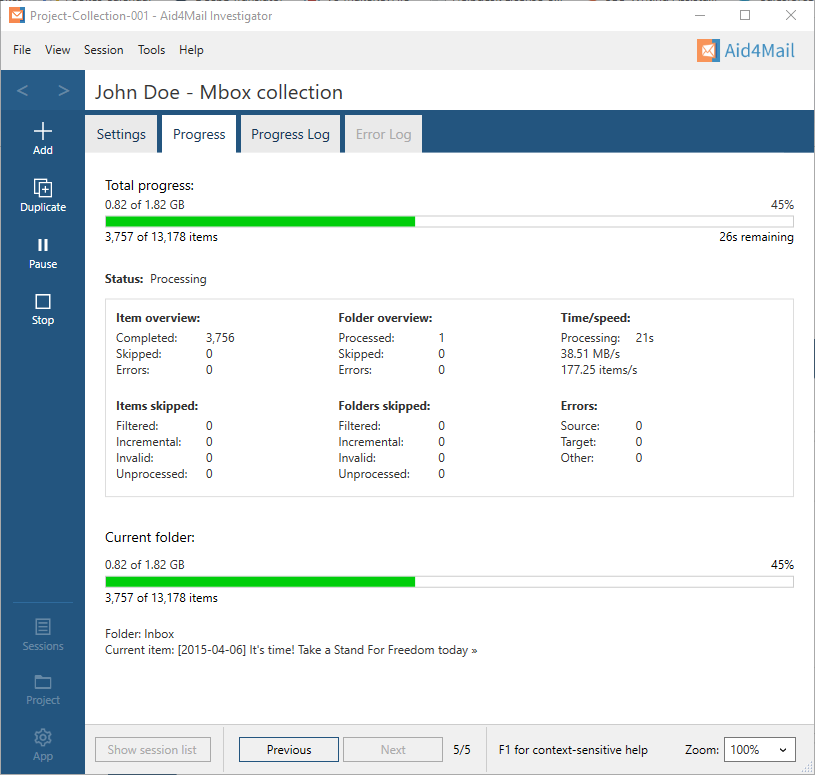
Superior Forensic Email Recovery
To ensure a successful email forensics investigation, you must collect as much relevant evidence as possible. This includes emails a suspect has deleted, and emails contained inside damaged or deleted files.
Aid4Mail Investigator and Enterprise integrate email carving capabilities that outperform most forensic data recovery software. In other words, Aid4Mail can successfully recover more emails than digital forensics solutions costing thousands of dollars more. The quality of forensic email recovery matters—with the wrong tool, you might miss critical responsive ESI.
Double-Deleted (Unpurged) Emails
Aid4Mail Investigator and Enterprise can recover double-deleted emails (unpurged mail). These emails are no longer available in the Trash or Deleted Items folders. Aid4Mail can recover them from IMAP accounts, mbox files, and the Exchange Recoverable Items folder (for Microsoft 365 and other Microsoft accounts accessible through MAPI).
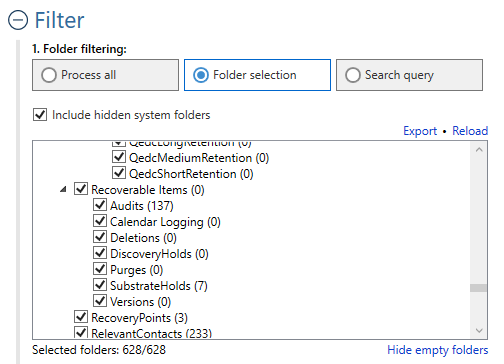
When people delete emails and empty their Trash folder, they may think they have hidden any wrongdoing. Don’t let them get away with it! Recover those double-deleted emails with Aid4Mail; you will find lots of responsive material.
Corrupted Mbox Files
The generic mbox file format (including mboxo and mboxrd variants) is widely used. Google Takeout and Google Vault use it for exports. Mozilla Thunderbird and SeaMonkey, Mutt, Elm, Nmh, and Evolution use it for native mail storage.
Unfortunately, the mbox format has a severe weakness. It is a straightforward database that stores emails natively, one after another, using a simple delimiter to identify the start of each message. It can be difficult to accurately identify the delimiter because certain programs create variations in the format.
An email may contain what looks like a delimiter but is not. This can result in a single email being misidentified as two or more. Bugs in client programs may cause delimiters or emails to save incorrectly in the mbox file, creating corruption. And, more rarely, issues with the computer file system or hard drive can damage the file.
Throughout the years we’ve been developing Aid4Mail, we have seen all kinds of corruption in mbox files. Every time, we have successfully developed methods to work around the damage. Our tests show that Aid4Mail systematically recovers more emails than competing solutions.
For one test, we created an mbox file containing the most common types of corruption observed over the years. Aid4Mail was able to recover all of its emails. We then compared the results with those from ten competing email recovery tools. The best recovered less than 82% of emails, and the worst just 30%. Averaging the results gave a 65% success rate for competing solutions versus 100% for Aid4Mail.
🛈 We’d be happy to provide you with a copy of the corrupted mbox file so you can conduct your own tests. Just contact us with your request.
Carving Out MIME Data
Aid4Mail Investigator and Enterprise offer a powerful carving tool that can uncover emails in forensically extracted unallocated space or an uncompressed disk image. In fact, they can carve out MIME emails from almost any file, including corrupt and unsupported mailboxes.
While these features are not unique to Aid4Mail, its performance is outstanding. In tests, Aid4Mail finds emails in unallocated space that other forensic email recovery tools can’t detect. It recovers whole emails when others only find fragments. Even if you already use a digital forensics platform with carving capabilities, Aid4Mail can be beneficial by finding evidence that these tools miss.
🛈 We’d be happy to provide you with a sample DD Disk Image file so you can conduct your own tests. Just contact us with your request.
Keyword Search and Filtering
Collecting the appropriate data and finding specific, incriminating information is crucial. Fortunately, Aid4Mail’s forensic email search and filter features are second to none.
In addition to basic folder filtering and deduplication, available in all editions, Aid4Mail Investigator and Aid4Mail Enterprise add email content search. This includes searching traditional attachments, cloud attachments, embedded files, and metadata.
Features range from basic date and keyword filtering, to support for complex search queries with Boolean constructs, wildcards, Regular Expressions, multilingual stemming, and more. You can also use AI to filter, classify, and even analyze emails.
Aid4Mail’s search engine is fully Unicode compliant and supports queries in any language, including non-Latin scripts like Greek, Arabic, Korean, and Japanese.
Native Pre-Acquisition Filtering
When accessing PST files, Gmail, Microsoft 365 (formerly Office 365), MS Exchange, or IMAP accounts, you can use Aid4Mail’s native pre-acquisition search to limit the scope of collected emails. This works by filtering mail directly on the server before downloading, or by filtering internal indexes in the case of PST files.
By narrowing the date range, and including specific keywords and message properties in your filter, you can avoid downloading unnecessary emails altogether. This will significantly speed up collection and acquire a higher ratio of responsive emails.
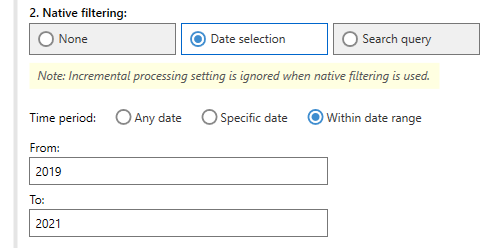
Minimizing the volume of emails retrieved from cloud accounts has a key advantage: it reduces the likelihood of service-provider data throttling. Throttling can significantly slow down email delivery or cap daily downloads. However, it can be effectively mitigated using Aid4Mail’s native pre-acquisition filter, circumventing such frustrations.
⚠ Beware of email forensics tools that have an undisclosed search cap, which may significantly affect your results. For example, a popular forensic email collector we tested could not retrieve more than 500 emails from a Gmail account. The software reached this cap without warning, and hundreds of emails were missing from the collection! This does not happen with Aid4Mail.
Search Syntax and Features
Aid4Mail does not rely on concordance indexes for its search and filter capabilities. Instead, it uses a fast, live search engine that operates on emails as soon as they are collected. The search syntax is easy to learn, similar to that of Gmail and Microsoft 365.
Search queries can include:
- Fielded searches (search specific parts of each email including attachments and file metadata)
- Boolean constructs (AND, OR, NOT, etc.)
- Comparisons operators (>, <, =, <>)
- Proximity searches (like Google’s AROUND and Microsoft’s NEAR operators, and more)
- Deduplication
- Wildcards and Regular Expressions
- Multilingual stemming (up to 24 languages) and tokenization
Aid4Mail search queries offer unique features that even Google and Microsoft cannot match! For example:
- Filter out non-personal emails (bulk mail, mailing lists, etc.) with a single operator.
- Filter emails by the day of the week or time of day they were sent, irrespective of the date.
- Find two search terms within the same sentence or paragraph instead of arbitrarily deciding how many words separate them.
- Use keyword search lists that can include thousands of simple or complex criteria. Aid4Mail includes several sample search lists that are customizable, or you can create your own from scratch.
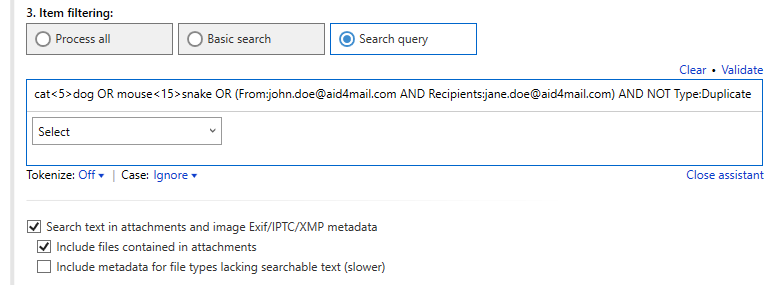
AI filtering and classification
Aid4Mail’s AI integration enables email filtering with unparalleled accuracy, going far beyond simple keywords to understand meaning and context. It can also classify emails into relevant categories, streamlining your review process, and organizing evidence with unprecedented efficiency.
Using AI to filter and classify in Aid4Mail offers significant advantages over traditional methods which can be time-consuming, expensive, and prone to missing crucial evidence.
- Enhanced Accuracy: AI-powered filtering, driven by well-crafted prompts and appropriate models, produces more accurate results than traditional keyword searches. This reduces the risk of false positives (irrelevant emails) and false negatives (missing relevant emails).
- Easier To Create: Creating effective search queries with traditional methods (Boolean logic, proximity operators, stemming, etc.) requires a certain expertise. AI prompts are simpler to create and can often be improved with the help of AI itself.
- Multilingual Support: AI filtering and classification excel at handling multiple languages reliably, a challenge for keyword-based approaches.
- Streamlined Classification: Go beyond simple “relevant” or “not relevant” results. AI lets you classify emails into many categories, enabling efficient organization and targeted review.
Aid4Mail leverages powerful AI models from OpenAI, Anthropic, Google, and Mistral AI, with more to come in the future. It also supports offline, on-premises AI models for handling sensitive information or when strict data sovereignty is required.
Aid4Mail’s incorporation of AI transforms your workflow from a laborious, resource-intensive process into a streamlined, efficient, and insightful operation. It offers flexibility and performance without compromising on security or compliance requirements. For further details, please refer to the Aid4Mail AI Integration User Guide.
Metadata and Attachments
Responsive data may not always be present in the message body of an email. Sometimes, it can be found in other parts, such as the header, attachments (traditional or cloud attachments), or embedded files (e.g., PDFs, pictures, and videos). Or even in metadata associated with these files. Therefore, examining these elements can provide valuable insights and help conduct effective digital forensics investigations.
Email header metadata
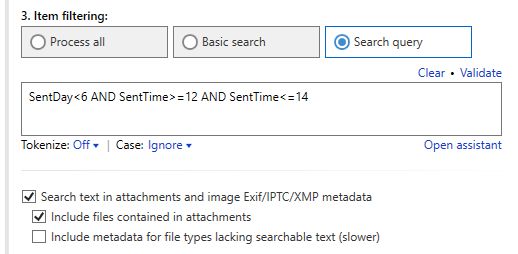
Aid4Mail provides fielded search operators, acting on email header metadata like the sender, recipients, date, etc. Unique operators enable you to search for emails sent on specific days of the week, or times of the day. For example, you can find all emails sent over lunchtime during workdays.
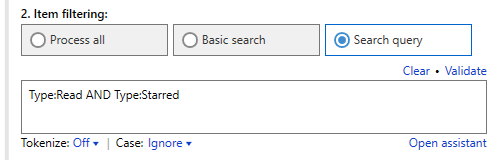
Email status information is valuable metadata, rarely exploited during investigations because many digital forensic tools don’t support it. Aid4Mail does and offers a search operator specifically for status information. Use it to exclude unread emails, or only collect flagged/starred emails, for example.
Traditional attachments and their metadata
Aid4Mail can search the contents of attachments and their metadata recursively. This means it can continually dig deeper into a nested structure of attachments in order to find search terms.
For example, if:
- An email has an attachment that is another email message
- The attached email has its own attachment, a ZIP file
- Inside the ZIP is a PDF file
- The PDF contains the text being searched
Then Aid4Mail will find the searched text!
Similarly, if:
- An email contains an attached ZIP file
- Inside the ZIP is another email
- This second email contains an attached TAR archive
- The TAR archive contains an image
- The image metadata contains the searched text
Again, Aid4Mail will find it!
Cloud attachments and their metadata
Aid4Mail Investigator and Aid4Mail Enterprise both support the collection and searching of cloud attachments (modern attachments), including those stored on Microsoft OneDrive (Personal, Business, or SharePoint) or Google Drive. Document revisions are accessible when necessary as are all associated metadata.
Cloud attachments can be specifically targeted in searches using the “Has” fielded search operator. You can target all cloud attachments, or only those from a specific platform. Combine this with date and keyword queries to pinpoint exactly the required files.
Filtering with Python
Aid4Mail’s support for Python scripts enables you to completely customize filters and add new features. Here are some examples of what you can do:
- Integrate OCR capabilities into your search or scan images for nudity.
- Perform sentiment analysis on email content to gauge the emotional tone or intent of communications.
- Implement language detection to aid investigations involving multilingual communication.
- Use IP geolocation libraries to trace the physical locations associated with IP addresses, in email headers, to determine sender locations.
- Identify and cross-reference social media profiles mentioned in emails, to link email identities with online personas.
Accurate Email Conversion and Data Extraction
Significant time and effort have gone into making Aid4Mail one of the most versatile and accurate email conversion tools available. Its high-end email parser can convert messages, their contents, and metadata into a variety of formats for review and analysis with other tools.
Data Integrity and Preservation
During the acquisition, review, or production phase, a forensic email collector must usually convert email from one format to another. If not performed correctly, significant data loss can occur. Certain format conversions are more prone to this than others, notably conversions between Outlook files (PST, OST, and MSG) and MIME formats (mbox and EML).
Data loss can affect various aspects of email data. The following may be missing altogether:
- Embedded images and attachments (both traditional and cloud attachments)
- Original email SMTP header and Message-ID value
- Sender or recipient email addresses
- Message status information (unread, read, replied, etc.)
Other parts of the email may be present but incorrectly converted:
- Folder names
- Dates, especially time zones
Data loss is sometimes unavoidable due to the constant evolution and complexity of mail systems and formats. However, it can be mitigated by using a specialized and up-to-date email forensics tool like Aid4Mail.
Aid4Mail’s conversion engine boasts over 25 years of expertise and is updated regularly to respond to changes in the products it interacts with. In conversions between MIME and Outlook formats, Aid4Mail outperforms most of its competitors. It is one of the few tools that can convert native Apple Mail files (EMLX) without any data loss, as well as Thunderbird and RFC 1521 emails with “detached” attachments.
We know how to preserve data integrity, that’s how we built our reputation!
Email Backup Option
Sometimes, format conversion fails due to issues with the target API (typically with MAPI or IMAP). When this happens, it is essential to have a backup of the source email for preservation purposes.
Aid4Mail stores email backups locally under a folder structure that mirrors the source account. Emails collected through Outlook, or from PST and OST files, are backed up as MSG files. Emails from other formats are backed up as EML files.
Journaled Emails
Organizations use email journaling to create and maintain a secure and tamper-proof record of all email communications. They do this to satisfy compliance and legal requirements, as well as for data retention and disaster recovery.
A journaled email comprises:
- The journal envelope, containing:
- A header with essential metadata such as sender and recipient addresses, timestamps, and transport information.
- A body with the journal report that typically includes sender and recipient addresses (including Bcc and distribution list recipients) and the original Message-ID value.
- An attachment containing the complete, unaltered original email message.
In an investigation, journaled messages present several challenges. For example:
- Depending on the email client program, the original message is shown as an attachment, and so can only be accessed after extraction.
- When using fielded searches on header metadata, important information only available in the original email header, or journal report, may be missed.
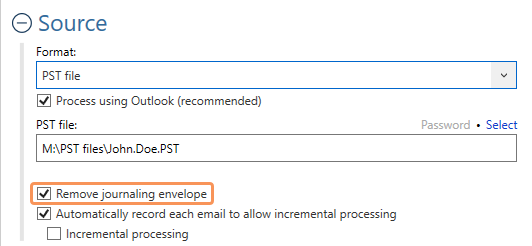
Aid4Mail solves these challenges with two unique features:
- Removes the journaling envelope during collection.
- Preserves essential metadata by adding the sender, and all recipient addresses, from the journal report to the original email header.
Review and Ingestion Formats
Aid4Mail can convert emails to formats commonly used in email forensics investigations. These include PST, PDF, CSV, EML, and mbox, as well as more unusual formats like HTML, XML, JSON, and plain text. PST files, frequently used for ingestion into an eDiscovery platform, or for review in Outlook, are by far the most popular format.
Emails are often converted to PDF files, a convenient format for presenting evidence in court or sharing with others. Aid4Mail offers standard PDF as well as variants—archivable PDF/A and press-ready PDF/X. You can insert Bates stamps into PDF pages, embed attachments in their native format, password-protect files, and more.
By converting emails to HTML, you can view them in any web browser, rendered as in a mail app. Attachments are stored separately in their native format, relative to the HTML file, and accessible from a link in the email message. You can even customize the HTML data to fit your requirements.
Aid4Mail includes a convenient HTML email viewer. It displays a list of all available emails as well as the content of the selected item. You can filter emails by folder, or by keywords in the date, subject, sender, and recipient fields.
You can upload the HTML output to a website and share the link to the viewer page with others. Your audience can then access faithfully rendered messages, and attachments in their native format. Don’t forget to scan all the files with an anti-virus before uploading.

Data Extraction
To perform metadata and attachment analysis in your investigation, you will need to extract relevant data from emails. Aid4Mail offers flexibility and complete control over this process.
Its high-end email parser can reliably extract:
- Traditional email attachments
- Cloud attachments
- Embedded message content (like inserted pictures)
- The message in plain text format
- Available message metadata, including the sender IP address
- Unique email identifiers, including PR_ENTRYID and EDRM MIH values
- AI analysis of the email. For example, this might be an automated summarization, translation, or extraction of specific criteria, depending on the prompt used.
Aid4Mail’s configuration editor enables you to choose exactly which data to extract.
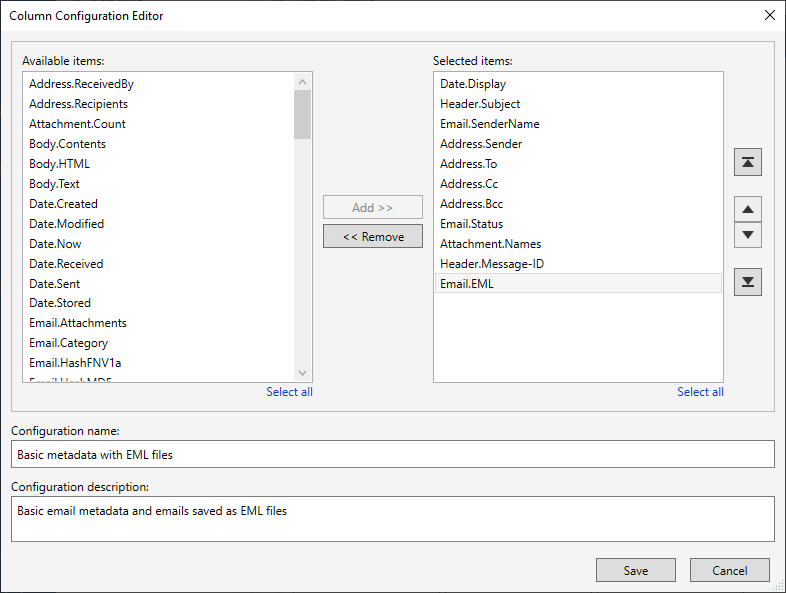
Extracted attachments and embedded contents are saved in their native formats (except for native Google documents that are converted to their Microsoft counterparts). Metadata and message text are saved in CSV (comma-separated values) files, either database-compliant or Microsoft Excel-compliant, or as TSV (tab-separated values) files.
Ease of Use and Accessibility
Aid4Mail offers a friendly interface for performing conversions quickly. And, unlike many other digital forensics tools, Aid4Mail supports high-resolution displays and provides accessibility features. You’ll also find plenty of resources to help with your email processing tasks.
Get Help When You Need It
We’re known for our award-winning customer support! All editions of Aid4Mail come with:
- Context-sensitive help with a description of each setting. Press F1 in Aid4Mail to open it in the right place.
- A comprehensive user manual, available in PDF and Windows Help (CHM) formats for offline use.
- A large selection of online Knowledge Base articles.
- An AI chatbot on our website that can answer most technical questions within seconds.
- Access to our Helpdesk, which typically responds to questions within a few hours.
Accessibility Features
Aid4Mail includes accessibility features to provide a more inclusive and user-friendly experience for a broad spectrum of users. This includes people with disabilities and anyone who finds such features beneficial.
High-contrast mode and a user-interface zoom assist users with visual impairments. Those with cognitive disabilities or mobility impairments can navigate the interface with a keyboard or dictation instead of a mouse. Screen readers, like Windows Narrator, are also supported.
Aid4Mail vs. Other Forensics Tools
Aid4Mail specializes in emails and their attachments and can collect, find, and recover mail that other forensics tools miss—it is an industry leader in this domain. Due to this specialization, Aid4Mail’s workflow differs from traditional digital forensics software like OpenText Encase, Exterro FTK, and Magnet Axiom. By focusing on its primary tasks, collecting, filtering, and converting emails takes a fraction of the time needed by other computer forensics tools.
Here’s why:
- Once configured, Aid4Mail can operate without user intervention. There is no manual review stage to interrupt the streamlined workflow.
- Aid4Mail’s native pre-acquisition filtering can significantly reduce the volume of data downloaded from IMAP accounts and mail servers like Microsoft Exchange, Office 365, and Gmail.
- With no review stage between email collection and conversion, Aid4Mail doesn’t need to build search indexes. This saves a lot of time and system resources.
- Aid4Mail’s integration of AI to analyze emails can also eliminate most, if not all, post-conversion manual review.
As a result, you can process terabytes of email data, unattended from start to finish, fast and accurately. And, unlike hosted eDiscovery tools like Relativity, Everlaw, and LogikCull, the whole process can happen on-premises, so you don’t incur third-party charges for the volume of data collected and processed. This significantly reduces costs.
If you need to examine a small forensic email collection, Aid4Mail offers convenient searchable formats, enabling you to review with the optimal app for your chosen output. For example:
- PST files in Microsoft Outlook
- Mbox files in Mozilla Thunderbird
- PDF files in Adobe Reader
- HTML files in your browser
- CSV files in Microsoft Excel
- JSON files in an AI analysis tool
- Plain text files in a text editor
If you cannot cull your forensic email collection to an adequate size, consider transferring Aid4Mail’s output to a comprehensive eDiscovery platform like Relativity, Encase, Axiom, etc. Aid4Mail is an excellent complement to other digital forensics tools, thanks to its fast email collection, native pre-acquisition filtering, AI integration, and email recovery.
Why Choose Aid4Mail?
Fookes Software has been developing software since 1989. Our first email tool was launched in 1999, followed by Aid4Mail in 2005. We have more than two decades of experience processing email data, longer than any other vendor of email forensic tools.
All core functionality in Aid4Mail is developed in-house. As a result, you benefit from key features that are tightly integrated and optimized for speed. We are in complete control of our code, including major components like email parsing and conversion, the filtering engine and its search syntax, MAPI access to Outlook accounts, and even the IMAP protocol used to connect with services like Yahoo! Mail and AOL.
Important clients around the world rely on our software, and the numbers keep growing. They include:
- US government and law enforcement agencies
- Top law firms
- National libraries
- Prestigious universities
- Major financial institutions
- International NGOs
- Half of the world’s Fortune 50 companies
Unique Functionality Missing in Other Digital Forensics Tools
Aid4Mail has a number of features that you won’t find in competing tools or, if they exist, are less well implemented. These are presented here, listed by Aid4Mail edition. (For a detailed feature comparison between the three Aid4Mail editions, check out our Aid4Mail 5 feature comparison table in PDF format.)
1. Aid4Mail Converter
| Aid4Mail | Competing Products | |
|---|---|---|
| High-speed email collection and conversion engine | slower and less accurate | |
| Very fast native incremental processing | ||
| Process Apple Mail mailboxes in native format | ||
| Restore Google Takeout folder structure | ||
| Reliably extract emails from corrupted mbox files | ||
| Recover and preserve email status information | not at all or partially | |
| Remove the journaling envelope while preserving its metadata | ||
| Reorganize and group emails by sender, recipient, date, etc. | ||
| Remote authentication of custodian accounts | not common | |
| Export to JSON for analysis with AI |
2. Aid4Mail Investigator
All the unique features of Aid4Mail Converter, plus:
| Aid4Mail | Competing Products | |
|---|---|---|
| Collect cloud attachments | ||
| Native pre-acquisition search with cloud-based accounts and PST files | not common, results capped | |
| Search all mail formats using a Gmail and Microsoft 365 compatible syntax | ||
| Find two search terms within the scope of a sentence or paragraph | ||
| Filter emails based on the day of the week or the hour of the day | ||
| Exclude non-personal emails (bulk mail, mailing lists, etc.) | ||
| Use AI to filter, classify, and analyze emails | not common | |
| Reorganize mixed email collections by individual account owner | ||
| Forensic file-carving that accurately recovers MIME data from disk images, including slack space and unallocated space, and unsupported mailboxes | ||
| Recover MS Exchange items and unpurged mail from IMAP accounts, MBOX files, etc. | not common | |
| Collect mail from native Google Vault exports | not common |
3. Aid4Mail Enterprise
All the unique features of Aid4Mail Investigator, plus:
| Aid4Mail | Competing Products | |
|---|---|---|
| Collect mail from native Mimecast and Proofpoint exports | ||
| Command-line interface (CLI) for automation and seamless integration with other tools | very limited | |
| Licensing options for offline use, virtual machines (VM), servers, and USB key installations | less flexible |
Practical Applications of Aid4Mail in Digital Forensics
Aid4Mail offers a robust set of features that can significantly enhance digital forensic investigations. Here are several practical applications where Aid4Mail can be highly beneficial:
Email Recovery and Analysis in Legal Disputes
In legal disputes where email communication can serve as critical evidence, Aid4Mail efficiently recovers deleted or corrupted emails. Its capability to preserve the integrity of metadata ensures that the evidence is admissible in court. This includes cases of contract disputes, intellectual property theft, and employment litigation.
Corruption and Bribery Cases
Aid4Mail facilitates corruption and bribery investigations by helping law enforcement officials to identify incriminating emails. These may contain evidence of corrupt practices, bribery, or unethical communication between parties. Using Aid4Mail ensures that all relevant data is preserved and analyzed.
Corporate Investigations
Companies often need to investigate insider threats, policy violations, or data breaches. Aid4Mail can assist by sifting through large volumes of corporate email data to identify suspicious activities, such as unauthorized data sharing. Aid4Mail does this by analyzing email headers, attachments (including cloud attachments), and body content for specific keywords, dates, and patterns.
Fraud Detection
Aid4Mail enables forensic investigators to trace fraudulent activities through email, including phishing attempts, financial fraud, or identity theft. It does this by offering advanced search and filtering capabilities that allow investigators to pinpoint relevant emails quickly, even within vast datasets.
Cybersecurity Incident Response
Following a cybersecurity incident, Aid4Mail can be used to analyze email-based attack vectors, such as spear-phishing emails, that may have led to the breach. It helps in understanding the attack’s scope and methodology by examining emails for malicious links, attachments, or deceptive content.
Compliance Auditing and Monitoring
Aid4Mail supports compliance officers in auditing and monitoring email communications to ensure adherence to legal and regulatory standards, such as GDPR, HIPAA, or Sarbanes-Oxley. It can automate the process of identifying non-compliant emails and provide detailed data reports to be used as a basis for further action.
Intellectual Property Theft Investigations
In cases of suspected intellectual property theft, Aid4Mail can be instrumental in tracing the unauthorized distribution of sensitive information. By analyzing emails for specific file attachments, or keywords related to proprietary information, investigators can uncover evidence of IP theft.
Human Resources Investigations
HR departments can utilize Aid4Mail for investigations into harassment, workplace bullying, or other policy violations. It allows for discreet and comprehensive analysis of email exchanges between employees, helping to resolve internal disputes and maintain a safe workplace environment.
Missing Persons Cases
In cases of missing persons, Aid4Mail can analyze the email accounts of the missing individuals or suspects to uncover clues about their whereabouts, potential threats, or people they were in contact with before disappearing.
Human Trafficking and International Crime Syndicates
By analyzing email exchanges, Aid4Mail can help uncover networks involved in human trafficking and other international crimes. This includes identifying perpetrators, victims, and logistical details of the trafficking operations.
Each of these applications demonstrates Aid4Mail’s versatility and effectiveness in addressing a wide range of digital forensic needs, making it an invaluable tool for investigators and professionals in various fields.
Flexible Licensing Options
Aid4Mail licenses are available as monthly or yearly subscriptions, and allow you to process an unlimited number of mail accounts and files, no matter their origin. You will benefit from free software updates and our award-winning customer support during the license validity period.
If you’re not ready to commit to a full license, we offer a low-cost two-week Aid4Mail Converter license as an alternative to our free trial.
On purchasing a license, you will receive an activation code that gets you up and running with Aid4Mail within minutes of payment. After activation, trial mode is disabled, and your license is linked to your computer and Windows login account. See the Aid4Mail EULA for details.
If you need to run Aid4Mail on a computer that doesn’t allow Internet access, simply contact us for an offline activation code. There is no charge for this option but it is less flexible than online activation.
It is also possible to run Aid4Mail in a virtual environment. Pricing is determined by the number of concurrent users plus the total number of users and installations. Contact us for a quote.
If you’re ready to buy an Aid4Mail license, visit our Buy Now page for pricing details, an overview of each edition, and links to our online store.
Glossary
Attachment
A traditional attachment is a file of any type that is attached to an email by the sender. An email can have one or more attachments, or none at all. Attachments are included in the email itself, increasing its size, although are not part of the message body.
Cloud attachments (also known as modern attachments) are a newer concept. They are not contained inside the email. Instead, they are hosted by a cloud-service provider and hyperlinked from the email. In some cases, this is done by the service provider because the file size exceeds their attachment limit. In other cases, often with collaborative online documents, it is simply for convenience.
Application Programming Interface (API)
A method of communication between two pieces of software. Using a mail service’s API to access data usually offers benefits over using more general protocols like IMAP. For example, access to additional metadata, native filtering, and reduced bandwidth limitations. Email-related APIs used by Aid4Mail include MAPI, Microsoft Graph API, and Google APIs.
Digital Forensics
A branch of forensic science that focuses on identifying, collecting, preserving, analyzing, and presenting data from digital devices, such as computers, smartphones, and network servers. Its aim is to extract and examine digital evidence in a way that is legally admissible, often for the purpose of solving crimes or legal disputes.
Disk Image
A precise digital copy or snapshot of the contents of a storage device, such as a hard drive, SSD, CD, DVD, or USB drive. It captures the entire data structure, including all the files and folders, as well as system-specific information like the master boot record, file system, and partition table.
Disk Slack Space
Unused space on a storage drive that exists when a file does not entirely fill the space allocated to it. Storage on digital devices is organized into clusters (or blocks) of a fixed size. A file usually requires multiple clusters and does not completely fill the last one. The unused “slack” space may contain remnants of previously deleted data or random bits of information from the memory. In digital forensics, disk slack space can be a valuable resource for recovering hidden or inadvertently stored data, providing insight into previous activities on the device.
Double-Deleted Email
An email that has been deleted twice: first from the Inbox or mail folder, and then again from the Trash or Deleted Items folder.
Electronic Discovery Reference Model (EDRM)
A framework that outlines standards for the recovery and discovery of digital data. The EDRM model is used to guide the process of handling electronic data during legal proceedings, including phases such as identification, preservation, collection, processing, review, analysis, production, and presentation of digital evidence. It’s widely adopted by legal and IT professionals to ensure a clear and efficient approach to eDiscovery processes.
EDRM Message Identification Hash (MIH)
A standardized method of identifying duplicate emails across multiple data sets from any vendor platform that supports it. The MIH is an MD5 hash value generated from the email’s Message-ID metadata field. It offers a universal method to recognize identical emails, enabling legal and investigative teams to efficiently manage, review, and deduplicate email collections. This solution enables cross-platform duplicate detection without the need to reprocess data, saving significant time and resources. The EDRM MIH is intended to complement existing vendor-specific deduplication methods, serving as an additional tool for more effective email management in discovery, disclosure, and investigations.
Electronically Stored Information (ESI)
Any data or information that is created, stored, or used in digital form. ESI encompasses a wide range of data types, including emails, documents, presentations, databases, audio, and video files, social media content, and electronic records stored on digital devices like computers, smartphones, and servers.
Email Forensics
A branch of digital forensics focusing on the recovery and investigation of email as potential evidence in legal cases or security investigations. Email forensics involves the analysis of email messages, including their content, headers, attachments, and metadata. It is used to investigate cybercrimes like financial fraud, intellectual property theft, harassment, blackmail, and extortion, and plays a crucial role in any legal dispute where email is relevant to the case.
Email Message-ID
A unique string of characters in the email header, that identifies a message in the context of a particular email conversation or thread. The Message-ID is assigned by an email system when a message is created, and is used to track, reference, and relate individual emails. This helps to manage message threading and prevent duplication. In digital forensics and email analysis, the Message-ID can be crucial for tracing the origin and trajectory of an email.
Although each Message-ID is unique within its own data set, it may not be so across multiple datasets. The EDRM MIH provides a solution to this problem.
Email SMTP Header
Metadata in an email message, containing detailed routing information. The SMTP header is automatically generated and located before the email message body. Although there is no limit to what can be added to it, key elements include the sender and recipient addresses, timestamps marking the email’s path through multiple servers, and unique identifiers for each server. Email service providers use the SMTP header to authenticate the email sender, and to correctly allocate incoming mail. In email forensics, the SMTP header is an essential resource for tracing the origin and path of an email, identifying spoofing, and understanding the network behavior of email communication.
Email Status Information
Metadata associated with an email that indicates the actions taken on it. For incoming mail, this includes whether the email has been read, replied to, or forwarded. For outgoing messages, it indicates whether an email is a draft, and whether sent or unsent. All emails can also be flagged, starred, or marked as double-deleted.
Exchangeable Image File Format (EXIF)
A standard for storing information as metadata in image files. EXIF metadata is commonly used by digital cameras and smartphones, and typically includes the camera model, capture settings (shutter speed, aperture, ISO, etc.), and the image date, time, and location (GPS coordinates). It is useful for organizing and cataloging images, and can be crucial in digital forensics for verifying the authenticity and origin of photographic evidence.
Fielded Search Operator
A command used to narrow down search results by targeting a specific field or attribute of an email or document. It enables you to search for an element like the sender, recipient, subject line, date, or other metadata field.
File Carving
A process used in digital forensics to recover files from a storage medium (like a hard drive or memory card) without relying on the file system metadata. It is typically employed when the file system is damaged, incomplete, or unavailable (as in formatted or corrupted drives). File carving works by searching the raw bytes and reconstructing file data based on known structures, signatures, or patterns. It is particularly useful for recovering deleted files or extracting data from unallocated disk space.
Internet Message Access Protocol (IMAP)
An Internet Standard protocol (RFC 3501) supported by most email applications that enables direct access to mail on a remote server. IMAP allows multiple apps to access the same mail account, even from different devices. This feature is the main reason IMAP is generally preferred over POP, an older protocol that requires mail to be downloaded to the device.
Messaging Application Programming Interface (MAPI)
An API for accessing Microsoft Outlook and Exchange. Aid4Mail uses MAPI to read and write to Outlook profiles, and PST/MSG files when the “Process using Outlook” option is turned on.
Multipurpose Internet Mail Extensions (MIME)
An Internet standard for email messages that supports both data and metadata, non-ASCII character sets, multiple fonts, non-textual content, and multiple attachments of various file types. It is an extension of the original Simple Mail Transport Protocol (SMTP).
PR_ENTRYID
A property used in Microsoft Outlook and Exchange to uniquely identify various types of objects within the messaging system, such as emails, calendar events, contacts, etc. It is a binary value that acts as a unique key, allowing each item to be retrieved, moved, or manipulated within the system. This identifier is crucial for developers and administrators working with Outlook and Exchange APIs, or scripting, as it enables precise access and control over individual messaging objects within the store.
Responsive Data
Data that is pertinent to matters of the case (in a legal context) and meets the criteria specified in a discovery request. It can be in various forms, such as emails, documents, images, or other electronically stored information (ESI).
RFC 1521
An early part of the MIME standard that defines support for non-ASCII character sets, multiple fonts, and non-textual content. We refer to this standard when discussing certain types of attachments based on the Message/External-Body subtype format that Aid4Mail supports.
Simple Mail Transfer Protocol (SMTP)
A standard protocol for email transmission. Mail servers use SMTP to both send and receive email messages. Email client programs typically only use SMTP to send messages (to the mail server for relaying), using IMAP or POP to retrieve them. SMTP was created in the 1980s and has since been modified and extended multiple times. The version commonly used today is extensible, with extensions for authentication, encryption, binary data transfer, and internationalized email addresses.
Stemming
The process of reducing words to their base or root form. For instance, the words “running,” “runs,” and “ran” all stem from the root word “run.” This technique is used in search algorithms to improve their effectiveness, by allowing for the matching of word variants with a common stem. Stemming enhances the ability of search engines or text analysis tools to find relevant results when the exact form of a word is not known.
Tokenization
The process of breaking a string of text into smaller units—tokens—usually words or phrases. Tokenization helps to identify key elements in a text. It is fundamental in text analysis and search algorithms, where the tokenized text is used for further processing like indexing or evaluating search queries.
Unallocated Space
The areas of a drive, or other storage device, that are not currently assigned to any files or directories. This space may contain remnants of deleted files, temporary files, or data fragments that have not been overwritten. In digital forensics, unallocated space is a valuable resource for recovering deleted data or investigating past activities on a device.
Virtual Machine (VM)
The virtualization of a computer system that provides the functionality of a physical computer and its operating system. With enough computing power, multiple virtual machines can run independently from one another on the same underlying hardware.